Access to social networks is not something you place limits in these times. All networks are up and running 24/7, and even the strictest parents can’t avoid the presence of their kids in social media sort of taking away their phones or giving them an old model with no access to the internet.
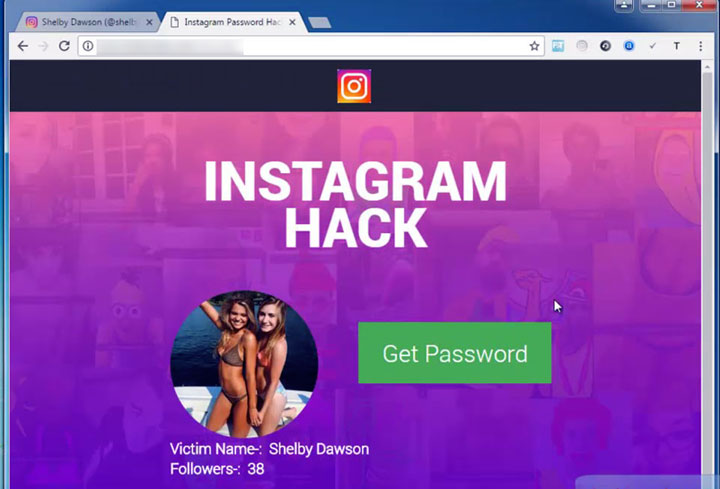
Facebook, Instagram, Twitter are the juggernauts that take away the attention spans of people all over the world for hours and meeting someone who doesn’t have some (more…)


 In this post I’m going to do an in-depth analysis about the email hacking software “
In this post I’m going to do an in-depth analysis about the email hacking software “